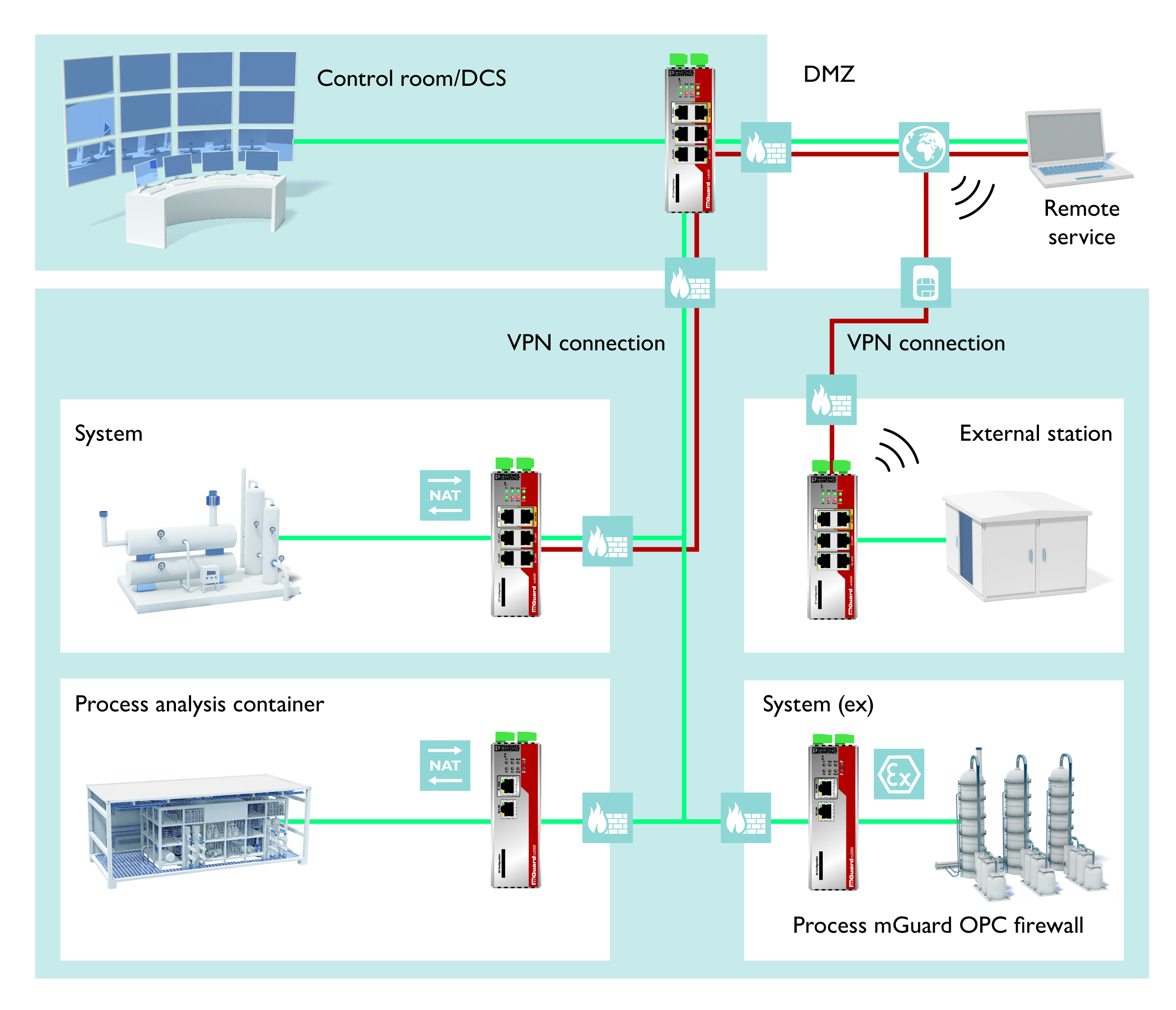
The factory of the future is characterized by the increasing networking of control technology, IT and IoT. The various systems must be seamlessly interconnected to ensure end-to-end digital processes. At the same time, however, this increases the risk of cyber attacks, as attackers have more and more entry points. In the connected world, attacks can cause more damage than ever before. It is therefore essential that security is consistently implemented at all levels. ctrlX AUTOMATION shows how this works while maintaining radical openness in automation.
More and more devices and machines are being networked and communicate via the Internet of Things (IoT). This creates numerous opportunities, but also risks. The more components are connected, the larger the attack surface. Cyber attacks can paralyze production and lead to financial losses and image damage.
Many systems in factories are outdated and were developed without considering cyber security. This makes them more vulnerable to attacks and difficult or impossible to update. It is therefore necessary to develop more resilient solutions. This must include IT systems as well as control technology and the IoT. This means: radical openness at all levels meets security at all levels.
But secure: from the control system to the apps
With ctrlX AUTOMATION, Bosch Rexroth has launched an end-to-end, open automation solution that has been designed from the ground up to be completely secure. The high security standards apply to all components in the automation toolkit and to every component by which the system grows. The hardware and software products are Secure by Design. This means that security requirements are already taken into account in the development phase. The automation solution, which was developed with a focus on conformity with IEC 62443-4-2, is based on the Linux Ubuntu Core operating system, which is considered to be extremely secure.
The ctrlX CORE controller is an example of the high level of security in the ctrlX AUTOMATION portfolio. The associated IoT software has fully integrated IT security standards according to IEC 62443-4-2 for access control and remote maintenance. In addition, the controller offers various security features such as Secure Boot, a security chip in accordance with TPM 2.0, and a minimal network footprint when delivered. With the optional firewall and VPN client, the controller can be upgraded to a full-fledged network appliance, which ensures the highest possible availability and security of the connected network components.
Since ctrlX AUTOMATION is not a self-contained system, but rather a place where different players pool their domain knowledge, the security strategy also includes the partner network ctrlX World. For example, each of the partner apps offered is validated by Bosch Rexroth. This rules out the possibility of third-party software introducing malicious code. This and the sandboxing principle further increase the security of the other apps installed on the system.
ctrlX developR design with a view to the future
The holistic and fundamental implementation of security standards and mechanisms in all facets of ctrlX AUTOMATION creates a resilient overall system that can also demonstrate these capabilities. In order to maintain this level, permanent further development is required – also in view of ever new types of attacks and ways of attack.
That is why ctrlX developR always keep their fingers on the pulse and look to the future. The latest security requirements are already taken into account in the planning and development phase. At Bosch Rexroth, “Two steps ahead” also applies when it comes to security.
If you have any questions or require further information regarding ctrlX AUTOMATION, please contact us: sales@cmafh.com
CMA/Flodyne/Hydradyne is an authorized Bosch Rexroth distributor in Illinois, Wisconsin, Iowa and Northern Indiana.
In addition to distribution, we design and fabricate complete engineered systems, including hydraulic power units, electrical control panels, pneumatic panels & aluminum framing. Our advanced components and system solutions are found in a wide variety of industrial applications such as wind energy, solar energy, process control and more.